I’ve never needed it before, but I think it’s time to find out.
What is Passphrase?
does it protect us?
Not really. Once chia is started, the RPC is not a protected channel - it is open for any requests in clear. The same with kbd/mouse macros.
If it didn’t arrive, that most likely would mean that when you pasted the address, it was somehow modified on the fly, implying that the shit is in memory potentially scanning clipboard.
On the other hand, if you see it hit your wallet, and then the next transaction removing it, that would suggest that they operate from a different box using your credentials. (In the first case, they could also lift your credentials.)
The first case doesn’t explain how wallets got emptied in the first place, as there was no initial transaction involved. So, maybe you missed something.
do you mean brute force?
As long as you define brute force.
If you have that shit active on the box, it can monitor chia’s RPC port. Once chia has started, the port will be open, and a couple of calls will lift mnemonics. Once that happens, that shit can delete itself making life harder to identify what it was. So, in my terms, there is no brute force there, just Chia’s incompetence to let the RPC be not password protected.
charges sent via the https://faucet.chia.net/ website to the old address: xch1ff3gdvxftn857fqnesy09m8xsj2s87szp29kxehfysl57n9tyfcqu7cx7l
They didn’t arrive at all.
Please try if you can send via https://faucet.chia.net/from your browser to xch1ff3gdvxftn857fqnesy09m8xsj2s87szp29kxehfysl57n9tyfcqu7cx7l
I am not touching any chia related websites today ![]()
This shit is really nasty, so the quicker people will identify what they used, so maybe we can find the pattern, the better. As I said, it is over 10% of wallets that are affected, and potentially that crap is still working on it. So, I would really refrain from using any chia related things (websites, etc.).
As it looks like this is a well-executed thing, it may be that they infected not just one place but many, and if people will start panicking, and checking stuff online, that could cause more damage.
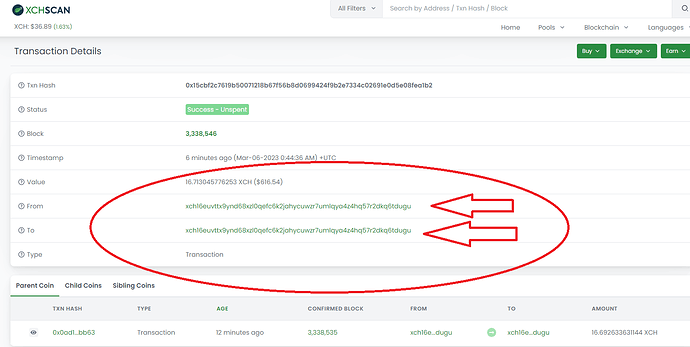
xch16euvttx9ynd68xzl0qefc6k2jahycuwzr7umlqya4z4hq57r2dkq6tdugu Balance:
15.446094939786 XCH⚠️
XCH value:
$565.94 (@ $36.64/XCH)
xch1zt476z4rh30fngvapdqjvlt9t0y5tr2x5em8d442xrp3q48kfwqql5z72c The current value of this address is 2785.821328734254 XCH ($101981.03).
funds are transferred from one address to the next address!
If the information about the hacker attack is confirmed tomorrow, we will have a price fall around 0!
Analyze the above 2 wallet addresses on your own and you will see that the attack started today and is STILL ON!
It is not easy to pull off a “good” tool, so this route is kind of hard to do, IMO. Also, going this route throws a shade on rather respected devs, what could be a big collateral damage. So far, we have seen some primitive things that were used by a handful of people, and those tools acted immediately. So, it is rather hard for me to cross that bridge (not saying that this is not the case, but still not too many tools are used by 10% of farmers).
Infected website or mobile app is a more palatable thing to me, but this has the drawback that multiple sites have to be infected at the same time (so also a hard scenario to pull).
Guys, I’ve been using chia practically from the very beginning. The farm is on a different computer than the wallet.
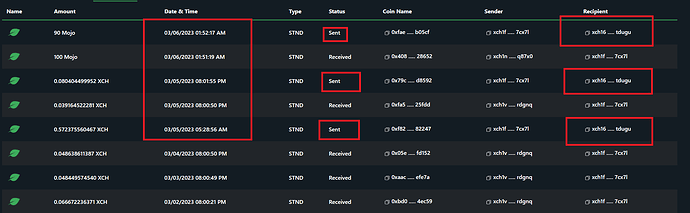
Farm connected to the pool - the pool pays daily coins that did not go to my wallet today.
After launching the wallet, I saw that all my funds were sent to an address that does not belong to me.
The computer has already been scanned with various antivirus programs and nothing has been detected
Hey, no one is beating on you. We are just trying to get as much info about what was used, … Maybe we can see some patterns.
More people need to chime in, as just a single account is not really revealing much, and is hard on that person.
Let’s see if more people are reporting the same issue. So check your xch wallet to see if you have all the coins in it. From what I can see, the xch coins are still arriving at the attacker’s wallet address.
There is no disagreement here. This thing had to land on the farmer or wallet to lift mnemonics. The question is what the delivery tool was, and I would not try to make any judgements what it could be, yet.
The only point I was trying to make is that to pull it off like that requires quite a bit of work (potentially for a single person).
Could you run via CMD netstat -ab in elevated mode on your farmer and wallet boxes and filter it for both chia and 9256 port.
In case this thing is active, maybe it will show up as clinging to that port (chia’s wallet RPC port - RPC Overview | Chia Documentation) That page has the list of all RPC ports for chia.
Send me a private message and I’ll send you a report
Look, please, who sends coins to himself? this is the last transaction from the wallet that took all my coins from me.
See how they work…
My wallet
look that everything that comes to it is immediately sent to the address of the attacker’s wallet
Currently, I can’t think of anything I could install or display in a web browser.
Also see that I’m not alone on this topic, someone else started this post today.