RUNE just recently lost $4.8 million worth of Ethereum (ETH) from its liquidity pools to an attack this past week.
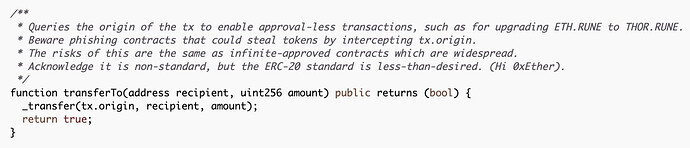
This only effected their ETH pools, however it was due to a simple coding mistake:
The standard way is to use msg.sender instead of tx.origin.
you → contract (you = tx.origin, you = msg.sender)
contract → rune (you = tx.origin, contract = msg.sender)
Sources:
Calling out the significant risks here imposed by smart contracts (i.e. the Official pooling protocol) that are unaudited by a third-party.
1 Like
Pretty sure the pool contacts are in the repo if you want to go read/audit them. I’ve been meaning to learn lisp.
1 Like
Yep, we read them over and seemed fine. Obviously nothing is 100%.
1 Like
Looked through all the repos on Github and didn’t find anything in the pool-reference.
Please share as I’m happy to take a look. Appreciate the positive attitude!