It requires a little more subtlety as with this simple approach the hacker could “poison” addresses with small amounts of XCH. There was a lot of this going on when the Ethereum mixer Tornado cash was sanctioned by US OFAC. But I’m working on providing solutions for this problem with a specialized partner.
Thank you, I didn’t think about that.
Could you maybe dump all those transactions where that address is the receiving one and see how many unique addresses are there? If that would be not too much, maybe check how many unique with XCH more than say 1XCH or so (just pick a number that looks sound).
No it is not enough to attack.
I do recall that there was an issue in the past where someone made a fake copy/lookalike of Madmax and/or Stotiks githubs and people were downloading bad software, but I only heard it as a rumor.
The attacker now moved all coins to this address: xch16l2n6tj0jvtks7mkvfkqf88xlh54rmtj8k7rlt5k4nqpt80z3tjqru4a5d - Chia (XCH) Blockchain Explorer | ALL THE BLOCKS (ATB)
Total of 4855 XCH
i know its not realistic, but it is theoretically possible to create afork with all transactions from these 3 addresses reversed?
One could still track the heritage tree of the coins which is independent of any wallet addresses … at least for a while is this would quickly grow exponentially complex…
It’s possible to fork and rewrite from day 1 if someone wants to. Not going to happen for sloppy user security.
So, when do you think Chia will add password protection for accessing mnemonics / running transactions on a running node (GUI) and add password protection to RPC to close that sloppy security?
Wouldn’t hold my breath
Upcoming functionality will make a lot of these attack vectors moot. Clawbacks, multi-sig, rate-limit, etc… Be patient.
Welcome back.
I will remind everyone that I am one of the victims.
After losing coins yesterday, I generated a new chia address in the same wallet id. Then I transferred a small deposit to the new xch address and for over 7 hours the funds did not change hands.
Which throws up new attack ideas - the hacker only has access to 1 address xch has no access to 24 security words etc.
If the coins change hands, I will inform you here
Nothing really about the patience.
Since you agree that those attack vectors are there, I would think that those are potentially the primary reason to write those programs / scripts, as it is relatively easy to find people that are less technical. So, I don’t get why you have chosen the route to put the main blame on sloppy end user security ignoring these factors.
This is wrong. As it was stated already, the attacker has your mnemonics, as otherwise it would not be able to make those transactions. The attacker is only using a “dumb” / faster way of checking the wallet.
If I haven’t said it already, sorry for your loss and thanks for sharing all your info here. From everything you’ve shared it seems you did no do anything silly, but were just unlucky somehow and got targeted.
I’ve seen more people reporting that only the first address is being targeted which is weird, but still they would have to have access to the private keys to do the transfer, so that wallet is just busted and untrustable.
True cold wallet is still the only safe storage, or a hardware wallet when they become available.
Because 24 words responsibly generated and stored ARE secure. It’s not Chia’s responsibility to protect your keys, that’s YOUR job.
A single pvt key for the compromised address is enough.
Is it not?
Sorry, I missed that. You are right. However, either that key or mnemonics need to be lifted. My take is that the only way to have that happen is have the attacking code on the running node / wallet (so the same difficulty to lift both). I am not sure if there is any other way to lift pvt key for a given address other than talking to the node/wallet.
The attacker was lazy and is only checking the first address. Dont count your coins safe yet.
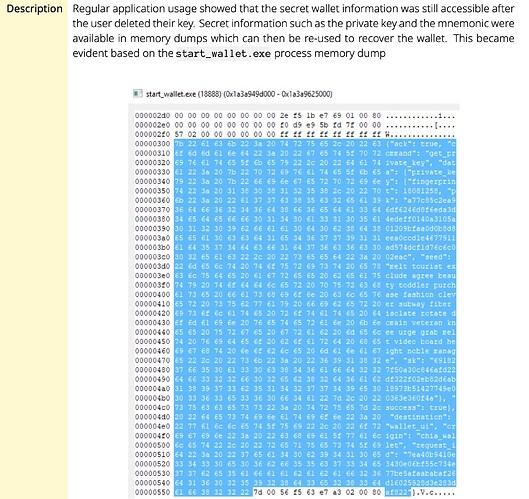
yes but those private keys are not stored anywhere, they are computed on the fly when needed based on the seed words.
that’s to be expected with a garbage collected language.
but even with C++ you need a secure memory allocator.
in any case, accessing memory from another process requires root permissions.