What is going on? After year of work they took everything? Is there any chance to find out who is under that?
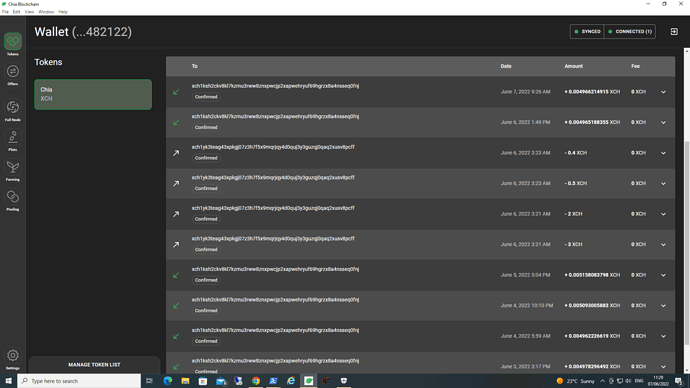
Can you copy and post the address they went to?
Will make it easier to search in an explorer.
Not likely.
Which pool are you on?
Actually in Core pool from beggining.
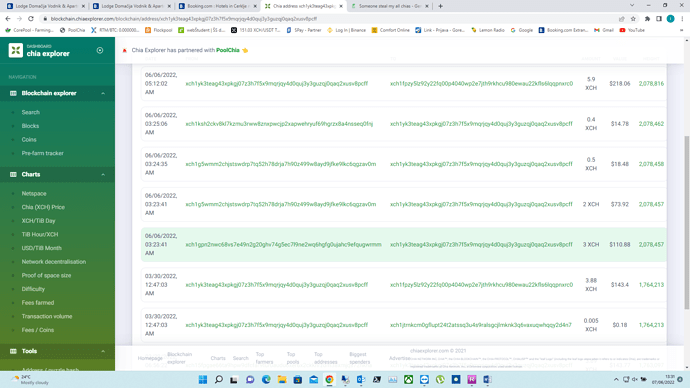
xch1yk3teag43xpkgj07z3h7f5x9mqrjqy4d0quj3y3guzqj0qaq2xusv8pcff
OG plots or NFT, are you running their client software?
Both, and yes ofcourse I am running Core pool software.
It seems your coin already left that address and got sent here.
Not much can be done now if your sure thats not your address.
I would consider your pc or keys compromised.
I have no clue how that pool works so cant offer any advice.
Sorry for your loss.
Edit.
In fact, searching a little further it would seem that address belongs to simpleswap according to this post.
You could contact them but i doubt it will help at all, they have probably already swapped the funds.
It is info you could take to LE if you chose to, but personally i wouldnt bother.
First off, sorry this happened to you. And the others are right, your computer is compromised. Either it is now or is has been in the past. Time to reformat.
For anyone that is reading this … no matter what your situation is, create and use a cold wallet. If you have ever used any third party tool on your system, do not create that cold wallet from that system. If you have ever used any third party tool or software, assume your system is compromised. Whether it is or isn’t is beside the point. Because if you just sit around and say “well, my chia is still there, must be fine”. Go ahead and have a chat with the OP here. I can guarantee his system was not compromised yesterday. That person sat around and waited until there was enough (in their eyes) to take. Knowing that once he attacked he would be exposed. Strike first. Create a cold wallet and move your XCH. NOW!. Until there is a hardware wallet with XCH support, this is your best option.
We have all put way too much time and money into this adventure to just have someone walk off with it.
I think they have some og plots, they can no doubt farm till replotted as long as rewards go to a cold wallet and maybe use self farming rather than pool farming ( i believe thats what they were doing but could he wrong).
Sorry to hear this, that really sucks ![]()
Definitely wipe that PC and start fresh as they have access to your wallet mnemonic or access to your PC so consider both compromised.
This has been an issue with most crypto currencies but I believe Chia has something in the roadmap to help prevent this from happening with delayed transactions in the future. Best thing to do now is to setup a cold wallet and start transferring XCH there from now on. Let us know if you need some instructions for setting that up.
Don’t use the pool’s mining software, they will automatically change your farm payment address and if you win 2XCH, it will go directly to their wallet. This is a historical legacy of the OG pool, which can prevent a farmer from mining together in multiple mining pools.
I’ve said it so many times. If they would just add Two Factor Authentication as a requirement when making a transaction, the problem would go away. The crazy thing is, that code is readily available. It wouldn’t take them a day to implement.
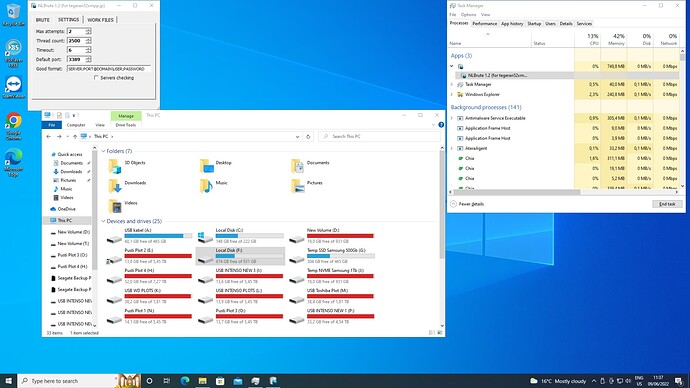
So I find out how they come in, by RDPwrap, and using nf user, check all if you have same user in computer, actually I cracked the pass to log on and thats the picture from desktop. Can not belive it happens…
And they are using Atera Agent…
Any idea how rdp wrap got on your system?
Its not part of window’s afaik.
Ah, maybe it is on some…
You can install the Remote Desktop app on any edition of Windows 10. However, the remote desktop protocol (RDP) that allows connections to a device is only available in the Pro edition and business variants of the OS. Windows 10 Home doesn’t allow remote connections.29 Apr 2022
Source.
So it would seem win 10 home is safe so long as you dont install rdpwrap .
It’s good that you are digging to see how it actually happened. But no matter how far you go, I highly recommend formatting that system. If they were able to get in there and install all of that there is a huge possibility that there is something else there that you don’t see that will let them do it again. Possibly many things you don’t see that leaves them a back door. Even the possibility of this is reason enough to go with a clean slate.
BTW, what third party chia tools/software have you had loaded on that system? It may be something you only tried for a moment. Could you list them out for us?
I cannot say that I know it for sure, but I was using RDPWrap before for a long time, and that was a good program. Maybe you have downloaded a fudged copy of it somewhere, not directly from RDPWrap page?
If you check the github page, the last time it was modified it was 4 years ago. Also, looks like there are no people complaining on the Issues page there. Although, it may be that when it runs, it try to load some missing libraries, and that part was hacked.
Id never even heard of it, but this is enough to put me off.
Yeah, I hear you loud and clear. However ![]()
I would also highlight the very first sentence from that article - “Some Chinese thin clients …” And that is what my original question was, whether it was downloaded from that page or rather as a part of such “Chinese” think client. Whether the RDPWrapper does the harm, or rather some other crap is using it (whether by bundling it, or asking the user to install it).
Also, RDPWrapper is not really “adding” anything to your Win system. What it does (or was meant to do when I was using it) was to let your Win Home use RDP protocol (using Microsoft libs) the same way one can use it on Win Pro. When I was looking at it, it was not downloading anything to your box. Saying that, if one has Win Pro, the RDP protocol is already enabled there, so those “Chinese thin clients” don’t need RDPWrapper to operate, as the “vulnerability” is already there.
Also, contrary to what is stated in that article (again, that was few years back), I have never had to "roll back security updates, … So, that is something new what I do agree that should not be done.
So, this is a bit similar discussion to stating that UPnP is the source of security issues. Well, yes it can be used in a malicious way, as long as one keeps downloading crap and blames everyone else for what happens next.
By the way, I used to have it on one old box that was running Win Home. However, I repurposed that box to be Fedora, so don’t have Win Home here anymore.
Saying all that, I would not mind paying $20 for the official RDP server coming from Microsoft that would enable Win Home to be able to run RDP server. I was looking for such option, but couldn’t find it. This is how I stumbled on XRDP (for Linux).